 |
1629 K Street NW, Suite 311
|
 |
"When you have eliminated the impossible, whatever remains,
however improbable, must be the truth"
Sherlock Holmes, literary Consulting Detective
Our services include:
|
"Paul Drake" for the following "Perry
Masons"
"Shaddock is a very conscientious and thorough investigator."
"No one gathers evidence and organizes it better for me than
Shaddock."
References |
||||||||||||||||||||||||||||||||||||||||||
High Tech Crime Network
|
Windows, Netware, DOS, Macintosh, Android, Palm, Palmtops, PDAs, Zip dives and other storage media
Some recent cases
Considering the evidence in the conference room to solve a client's case of
computer hacking
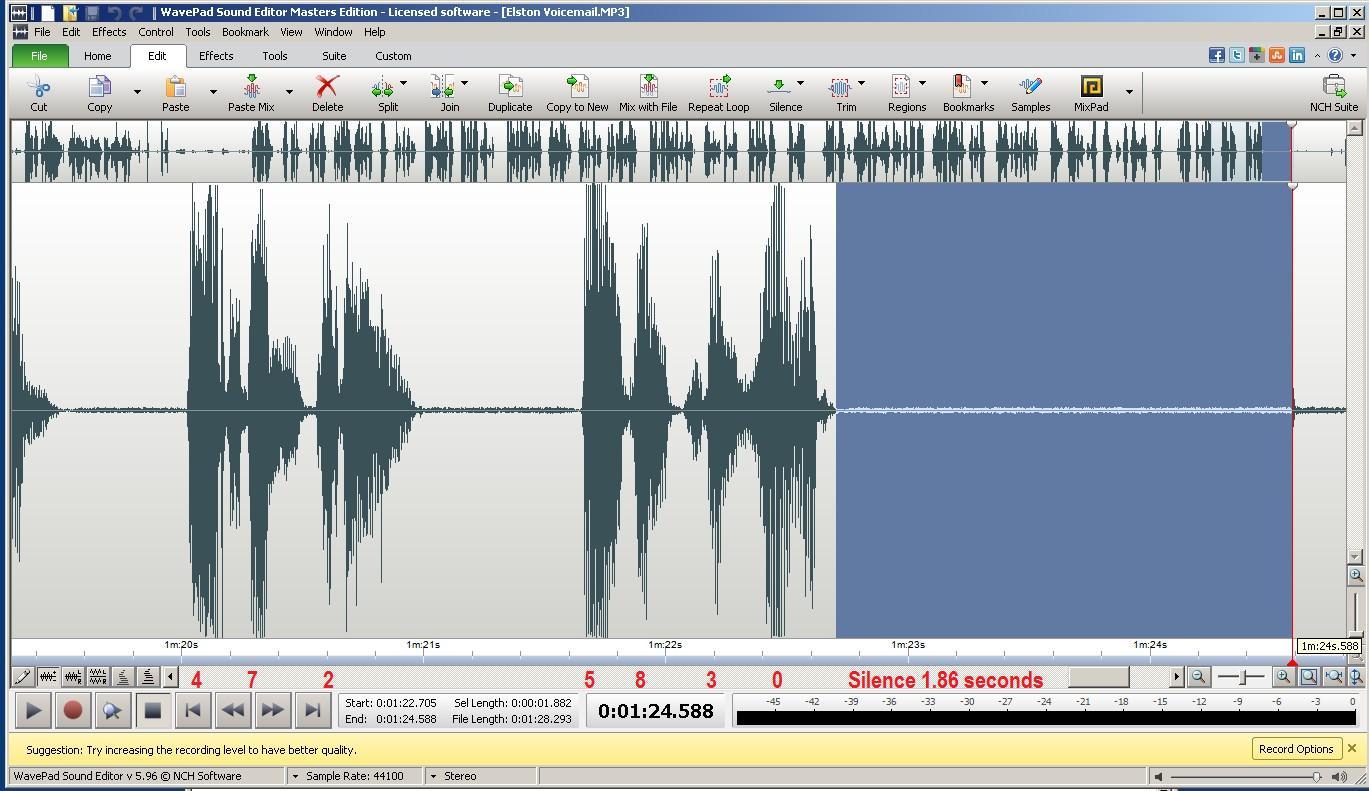
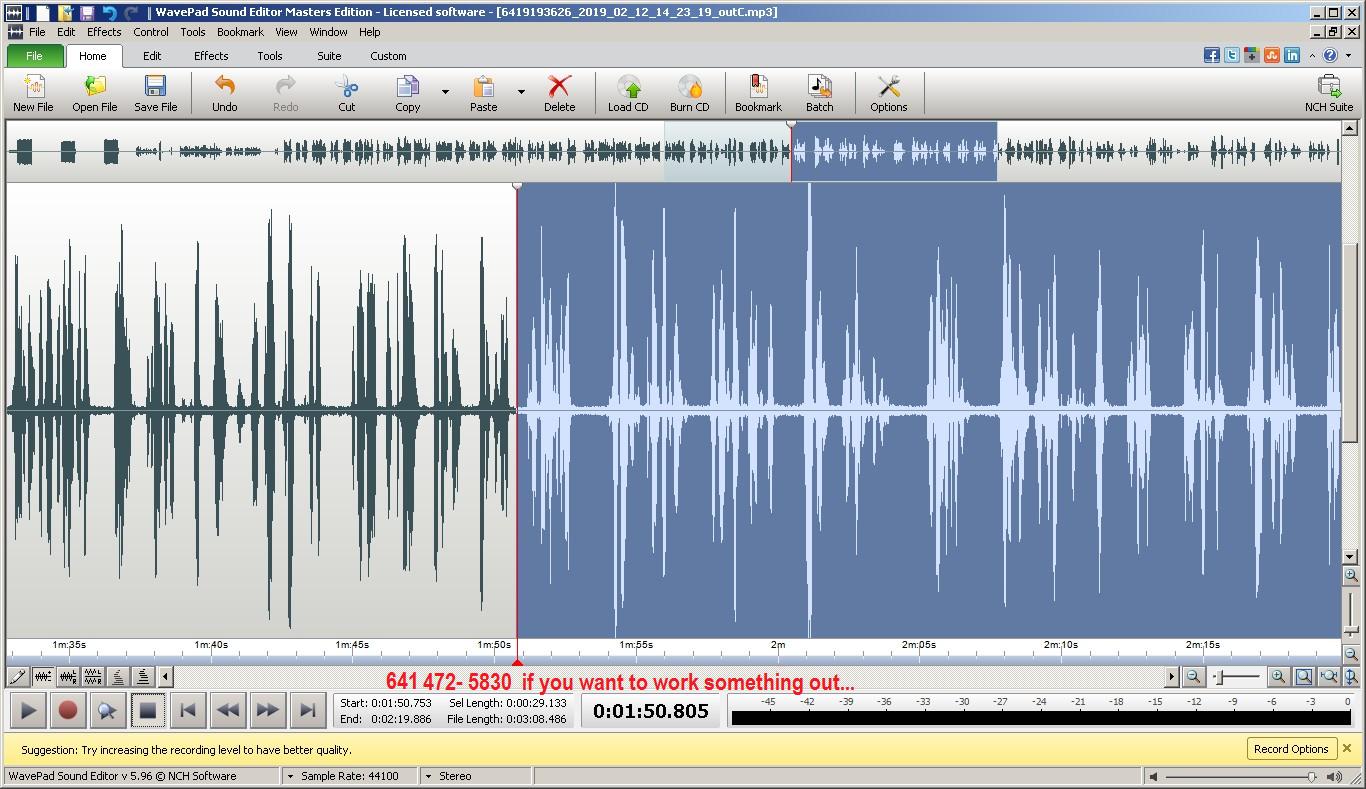
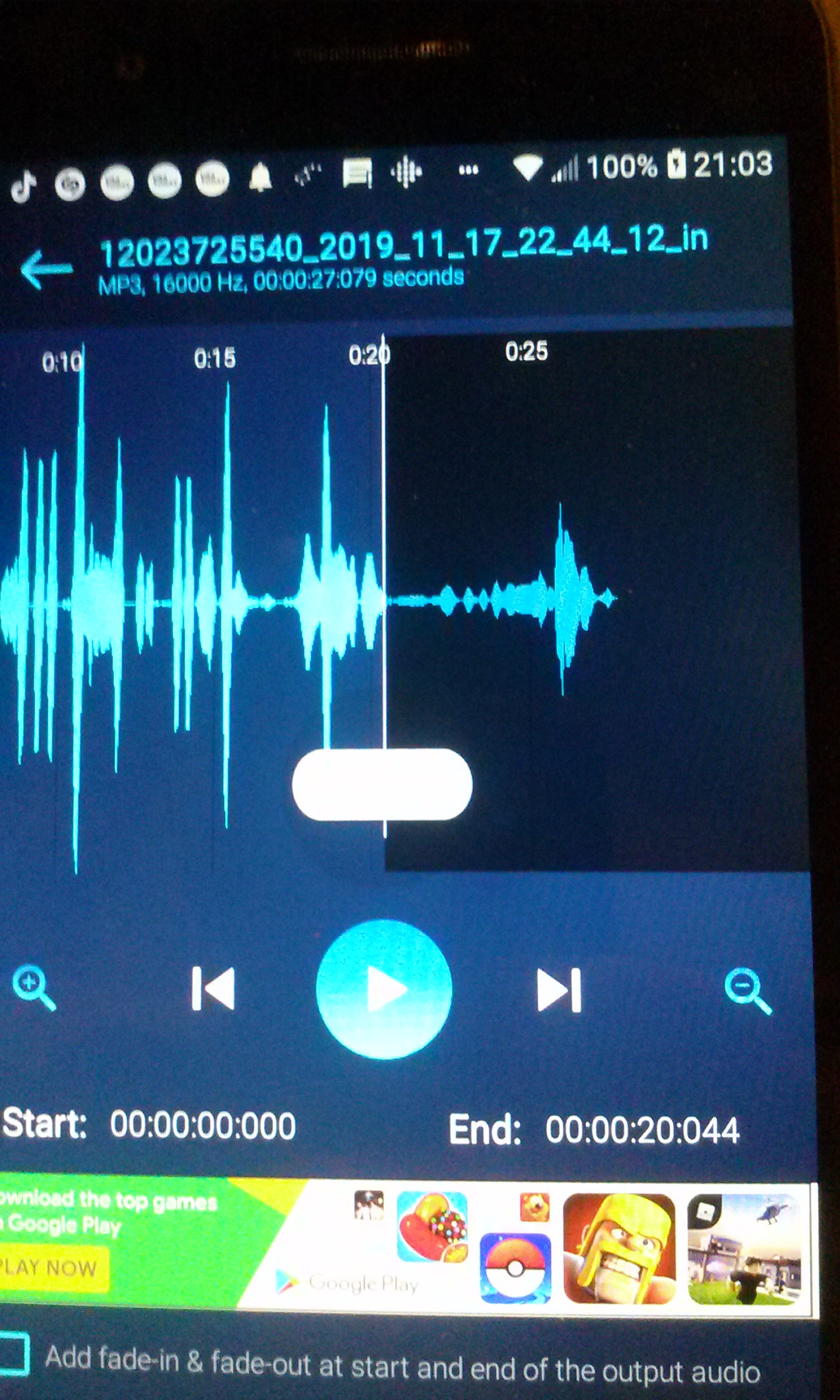
We proved that a felony phone threat suspect was innocent
because voice mail was truncated.
We proved an abusive husband forged the signature on
his wife's $100000 Life Insurance Policy,
sold her car without her knowledge, left her a car with bad brakes, contributing
to her fatal accident.

We proved a company owner falsely accused a former employee of
assault,
and created a computer generated voice "phone threat".
![]()
Computer Forensics
|
|
An impartial computer expert who helps during discovery will typically have experience
on a wide range of computer hardware and software. This is especially beneficial when your
case involves hardware and software with which this expert is directly familiar. But
fundamental computer design and software implementation is often quite similar from one
system to another, and experience in one application or operating system area is often
transferable to a new system.
Unlike paper evidence, computer evidence can exist in many forms, with earlier versions
still accessible on a computer disk. Knowing the possibility of their existence, even
alternate formats of the same data can be discovered. The discovery process can be served
well by a knowledgeable expert identifying more possibilities that can be requested as
possibly relevant evidence.
In addition, during on-site premises inspections, for cases where computer disks are not actually seized or forensically copied, the forensics expert can more quickly identify places to look, signs to look for, and additional information sources for relevant evidence. These may take the form of earlier versions of data files, such as memos and spreadsheets, which still exist on the computer's disk or on backup media, or differently formatted versions of data, either created or treated by other application programs.
| Protection of evidence is critical
A knowledgeable computer forensics professional will ensure that a subject computer system is carefully handled to ensure that:
|
|
Procedures
|
| Recovers all (or as much as possible) of discovered deleted files.
| |
| Protects the subject computer system during the forensic examination from any possible
alteration, damage, data corruption, or virus introduction. | |
| Discovers all files on the subject system. This includes existing normal files, deleted
yet remaining files, hidden files, password-protected files, and encrypted files. | |
| Reveals to the extent possible, the contents of hidden files as well as temporary or
swap files used by both the application programs and the operating system. | |
| Accesses, if possible and legally appropriate, the contents of protected or encrypted
files. | |
| Analyzes all possibly relevant data found in special, and typically inaccessible, areas
of a disk. This includes but is not limited to what is called 'unallocated' space on a
disk (currently unused, but possibly the repository of previous data that is relevant
evidence), as well as 'slack' space in a file (the remnant area at the end of a file, in
the last assigned disk cluster, that is unused by current file data, but once again may be
a possible site for previously created and relevant evidence). | |
| Prints out an overall analysis of the subject computer system, as well as a listing of
all possibly relevant files and discovered file data. Further, provides an opinion of the
system layout, the file structures discovered, any discovered data and authorship
information, any attempts to hide, delete, protect, encrypt information, and anything else
that has been discovered and appears to be relevant to the overall computer system
examination. | |
| Provides expert consultation and/or testimony, as required. |

Applications of Computer Forensics
|
| Criminal Prosecutors use computer evidence in a variety of crimes where
incriminating documents can be found: homicides, financial fraud, drug and embezzlement
record-keeping, and child pornography. | |
| Civil litigations can readily make use of personal and business records found on
computer systems that bear on: fraud, divorce, discrimination, and harassment cases. | |
| Insurance Companies may be able to mitigate costs by using discovered computer
evidence of possible fraud in accident, arson, and workman's compensation cases. | |
| Corporations often hire computer forensics specialists to ascertain evidence
relating to: sexual harassment, embezzlement, theft or misappropriation of trade secrets
and other internal/confidential information. | |
| Law Enforcement Officials frequently require assistance in pre-search warrant
preparations and post-seizure handling of the computer equipment. | |
| Individuals sometimes hire computer forensics specialists in support of possible claims of: wrongful termination, sexual harassment, or age discrimination. |

![]()
Where Can Clues Be Found?
|
|
![]()
|
|
Computer Forensic ToolsEncaseBasic WinZip TechniqueNorton UtilitiesCaller Id Spoof Awareness |
|
 Special storage device enables contents of seized hardware to be recorded without changing the contents |
 Recording data on CD enables the user to continue to use his or her computer during the investigation. |
High Tech Crime Network
|
|||||||||||||||||
National Forensic Center17 Temple Terrace Locating Expert Witnesses and Litigation Consultants Nationwide |
|||||||||||||||||
EnCase
|
EnCase Forensics Tools
|
||||||||||||||||
 |
We assist Dr. Lawrence Farwell
|
||||||||||||||||
Truth & Justice Foundation |
|||||||||||||||||
Enlightened Sentencing Project |
|||||||||||||||||
National Association of
Investigative Specialists
|
|||||||||||||||||
|
|
High Technology Crime Investigation Association |
||||||||||||||||
|
|
U.S. Secret ServiceBest Practices for Seizing Electronic Evidence |
||||||||||||||||
|
|
Department of DefenseComputer Forensic Laboratory - DCFL |
||||||||||||||||
 |
Leon Demsky, Esq.Attorney at Law, Arlington VADemskyLaw.com |
||||||||||||||||
|
Ian A. Williams, Esq.Attorney at Law, Washington DCIanWilliamsLaw.com |
||||||||||||||||
Robert Stone, Esq.Attorney at Law, Arlington and WashingtonBobStoneLaw.com |
|||||||||||||||||
|
Metropolitan Detective Agency |
||||||||||||||||
|
MDBInternational.com |
||||||||||||||||
EnCase CertificationThe recognized leader in computer investigation certification |
|||||||||||||||||
AccessData
|
|||||||||||||||||
MaresWare
|
Certifications of Dan Mares
|
||||||||||||||||
|
ContentWatch.com - free content auditThere are a number of ways objectionable material can find its way onto your computer without your knowledge or permission. Some of the most common ways are through receiving email, and intentionally or accidentally accessing inappropriate websites. This tool can help you avoid wrongful accusation. |
||||||||||||||||
HackerWatch.Org |
|||||||||||||||||
International Association for Cryptologic Research |
|||||||||||||||||
Symantec Security Consultants |
|||||||||||||||||
|
SpyWare |
||||||||||||||||
MaresWare.com - useful utilities |
|||||||||||||||||
|
WrongfulConvictions.org
|
||||||||||||||||
Paul J. RileyAttorney at Law, Washington DC |
|||||||||||||||||
Ken KleinAttorney at Law, Washington DC |
|||||||||||||||||
Ken Ketterhagen, Esq.Attorney at Law, Fairfield, IA 52556
|
|||||||||||||||||
|
Robert Shaddock, Esq.
|
||||||||||||||||
Brandon Nelson, Esq.Attorney at Law, Fairfield IA |
|||||||||||||||||
Scott SexauerAttorney at Law, Springfield VA |
|||||||||||||||||
|
|
CourtTV.com |
||||||||||||||||
|
Computer Instructors CorporationFACES and other computer software training |
||||||||||||||||
|
|
Dr. Joseph Bell Edinburgh, Scotland doctor and instructor of surgery of the late 1800's whose amazing powers of observation and deduction were Sir Arthur Conan Doyle's inspiration for the Sherlock Holmes stories. Dr. Bell helped Scotland Yard to stop Jack the Ripper |
||||||||||||||||
|
http://www.paraben-forensics.com
|
|||||||||||||||||
|
GlobalSat DG-100
|
Vehicle tacking services We place a device and provide a report of the whereabouts. |
||||||||||||||||
|
Domain-history.domaintools.com
|
You can get some clues from previous web sites | ||||||||||||||||
|
911Investigators.com
Investigating the Biggest Murder Mystery in American History |
|||||||||||||||||
 |
 Sherlock Holmes Sherlock HolmesRick has read
all
60 stories |
"I'm a consulting detective. I invented the job"
Sherlock Holmes