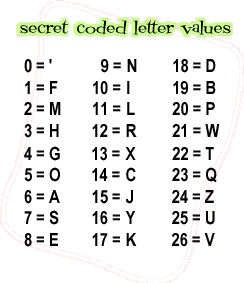
There are several easy techniques you can use to make it unrecognizable, by putting the numbers in a code. It does not have to be NSA-proof, but will foil those scanning for credit card numbers.
Credit card numbers usually have 16 digits, but we can disrupt this pattern.
Credit Card Encryption Technique |
Example using:
|
||
| 1. Additional Characters - Adding a random letter of the alphabet to each 4 digit sequence with a random letter or punctuation. The recipient simply ignores any non-number. | 1234A-5678B-90%12C-34?56D
Exp. 12E/10F or 1A2B3C4D-5E6F7Hello8There-9How0Are1You2-3456 |
||
| 2. Backwards - enter the credit card number backwards | 6543-2109-8765-4321 Exp. 21/01 | ||
| 3. Scramble 4 - Each 4 letter sequence is backwards | 4321-8765-2109-6543 Exp: 0121 | ||
|
1 =1 2 =A or B or C 3 =D or E or F 4 =G or H or I 5 =J or K or L 6 =M or N or O 7 =P or Q or R or S 8 =T or U or V 9 =W or X or Y 0 =Z or * or # Example: 1ADG-JMPT-WZ1B-EHKN Exp. 1C/1Z |
||
|
1 looks like a lower case L Example: |
NOTE: If you use a code, please use extra care to ensure accuracy and
consistency, so as not to delay the fulfillment of your order.
Thank you.